Identity Lifecycle | Provisioning | Access Management | Roles Management | Access Governance
Why: Most companies do not have a centralized access review in place where they can review who has access to what resources and applications. Lack of a centralized system forces the companies to do an access review at each system level which is very cumbersome and also tend to take a low-end approach to access certification by using excel's and email communication. This solution is a poor, manual, prone to errors solution.
Knowing and delivering exactly the right set of entitlements for every individual has always been difficult, and in today's complex and continuously evolving environments it is quickly becoming impossible-at least with manual tools and processes.
How : TSI's expertise in Compliance and Access Certification solutions helps organizations to come up with an automated access certification solution to centralize access details, automate review, strengthen controls, to assess and reduce risk.
These solutions enable the reviewers (Managers, Application owners) review periodically as to who has access to what in the organization and act upon in. For Ex during a manager review if a manager finds that one his reportees has access to a financial application which is no longer needed, he can mark that for removal and is captured as part of the compliance report. These actions can then be remediated thereby ensuring that the users have access as required only. Overall, Access Certification solution helps in reduce the cost of audits and regulatory compliance, promote management accountability for the authorization process.
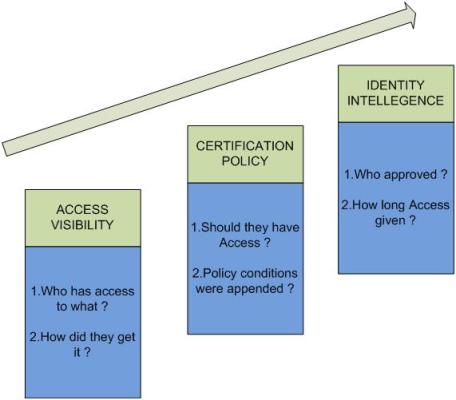
Tool Set:
Copyright © 2016. Technical Strategies Inc., All Rights Reserved.