Identity Lifecycle | Provisioning | Access Management | Roles Management | Access Governance
Why: Looking at the essential IT security administration processes, access control and granting access rights to users are of central importance. Managing authorizations is an onerous process.
In this context, the role-engineering issue is gaining more and more importance because it has become clear that role-based access control is the basis for what is today called "provisioning", i.e., the automation of identity-based security administration. The cost reduction and productivity potentials of automation and of more efficient manual administration are a high motivation for organizations to implement RBAC.
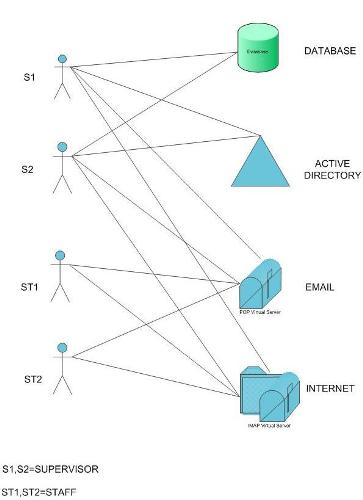
How : TSI brings expertise in Role Mining and Management solutions to bring organized migration process to RBAC with the goal of building a single point of administration and control, using various RBAC tools.
We present a process for detecting patterns in a data base of access rights and for deriving enterprise roles from these patterns. Defining a set of roles that is complete, correct and efficient is very important for practical implementation of RBAC.
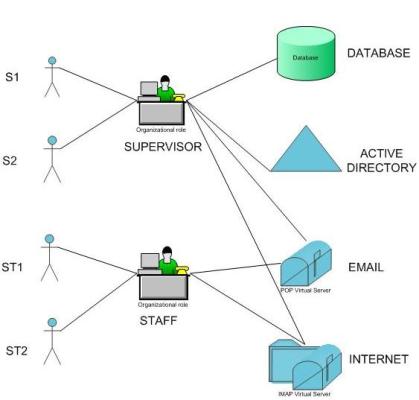
Tool Set:
Copyright © 2016. Technical Strategies Inc., All Rights Reserved.