Identity Lifecycle | Provisioning | Access Management | Roles Management | Access Governance
Why: Most organizations have redundant authentication interactions, multiple passwords which are difficult to manage, single authentication factors which are unsecure, no centralized monitoring and auditing.
Application security is a horizontal requirement across multiple applications, platforms, and infrastructure. In general, there's no business reason why Joe should need multiple usernames.
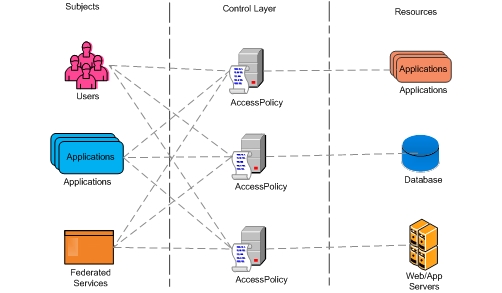
How : TSI's expertise helps organizations to implement access management solution and seamlessly integrate and extend access management solution to their applications. We follow a holistic, business-focused approach that incorporates our experience related to processes, control, technology and security with in-depth vendor software knowledge, to deliver a comprehensive and scalable access management solution.
This solution helps organization's to protect critical resources spread across various platforms and operating systems by enforcing policy based control. This solution provides multi-level authentication factors, Single Sign On mechanism, monitoring, auditing overall helping the organization enhance user productivity, avoid security breaches and help desk cost savings.
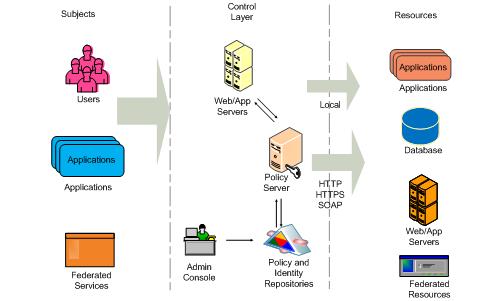
Tool Set:
Copyright © 2016. Technical Strategies Inc., All Rights Reserved.